What is true key application. True Key - automatic password management on every device. True Key what kind of program and how to remove
Intel Security is a modern company that is the developer of the True Key application. This service is a password manager. The utility supports devices with a variety of operating systems. Supported platforms include Windows, Mac, OS Android, and iOS.
The relevance of the software is that with its help it is possible to create unique passwords. If the user independently creates secret keys, then it is likely that they are quite weak. For this reason, crackers can declassify them quickly enough.
So it is important to create very complex secret keys that can secure the resources you visit on the network. When opening access to the site by third-party users, they can see all the information that is personal to another user. That is why it is so important to protect personal data.
Users often try to set their own passwords. This can be one secret key that will open access to all sites. It is very easy for fraudsters to crack simple passwords. For this reason, it is worth using special utilities.
A very powerful manager in this area is True Key. This software product is designed to perform several manipulations. First of all, it concerns password management. Users can create their own account and work with it free of charge.
Developers offer to work with accounts, the number of which can reach 15. But for this service you will have to pay a fee of $19.99. This price is for an annual subscription.
If users install some antiviruses, they will receive True Key as a bonus. This applies to users who choose to download Internet Security, Total Protection, and McAfee LiveSafe. These applications help in providing high-quality protection for a wide variety of devices.
True Key - an alternative to secret keys
The developer of this software came up with a plan whereby all users of the world would be able to stop using passwords. This plan can be implemented in three stages. At the first stage, it is planned to introduce all users to the use of password managers.
It is practically impossible to remember the developed secret keys if you do not write them down or use a special program for memorization.
The second step to achieve the goal is to completely stop working with passwords. The procedure for implementing this is only possible if non-unique secret keys are not used. In this case, you will need to use the services of generating passwords in a fully automatic mode.
Thanks to the received reports on security parameters, it is possible to reveal the real state of sites and other sensitive data. The report will list duplicates found, as well as fairly standard secret keys. Based on this, the program used will offer to automate the process of exchanging passwords for certain sites.
The last part of the plan is that the user no longer uses passwords, which will open access to many resources. This can only mean one thing: the authorization process is carried out without preliminary additional scanning of secret passwords. Thus, access to the site is provided instantly. Implementation of this plan in the near future.
True Key Features
With this application, users are given the opportunity to classify personal information. To use this utility, you must enter a master password when creating your own account. But this is not the only authentication method. You will also have to perform a few more manipulations.
Quite unique is that email can also be used as an authentication factor. This service sends messages to a previously specified mail account. Users will need to click on the link to unlock the database with passwords in an instant.
Immediately after successful authorization in the new device being used, you can define this device as trusted. If a user logs in from such a PC, then this is automatically proof of the user's identity.
Immediately after the process of installing the program on your smartphone, you can use this procedure as the next step on the way to authentication. As soon as the user tries to log into their own account, a request will be sent to the mobile device. After receiving it, just click on this notification. Immediately after this, the authorization will be considered successful.
There are also other options for its implementation. To do this, you need to use the front camera of the phone. By the face recognition function, it is possible to pass authentication. The user needs to remove the glasses for the process to succeed. This is proven by various tests.
There are special extensions that help in the registration procedure on smartphones. With the help of such plugins, it is possible to quickly recognize faces. This concept is much more efficiently developed thanks to the 1U Password Manager module. So even if the user looks away a little and raises his eyebrows, then in any case, authentication will be performed.
Also, users can refuse the proposed protection options. In some cases, users only need to enter a master password. This secret key can be changed at any time.
The advanced level of security involves the use of two protection options out of the three proposed. Just a couple of factors will help ensure the confidentiality of information. For mobile devices, you can choose between a master password, face recognition, or a fingerprint method.
If the user works with a desktop computer, then in order to gain access to certain sites, you must specify a master password, which is mandatory for any device, as well as another device. As soon as the user understands all these fairly simple manipulations, he can immediately add a trusted email account.
Further, the user will receive notifications in which he learns that if the main password is lost, access to data will be closed. Therefore, the information simply cannot be recovered. The uniqueness of the software is that even with multiple authentication, you can confirm your identity. In this case, the master password will be constantly reset.
The working process. Using a password manager
The first step is for users to install the software. This extension is a great helper for Chrome and Internet Explorer browsers. Very soon, a new version is planned to be released, which will be able to help users when working with Firefox.
This module in the next step requires users to create a password, which will consist of a word or phrase. You can compose a very strange phrase, which will be impossible to unravel. At the same time, the True Key manager does not have a standard repeated request for a master password.
The developers recently acquired a brand new manager that has already gained popularity. The PasswordBox program is used to bind to the account of the mail service of the same name. This is a very handy wizard. It will certainly help to transfer previously saved accounts.
Support for a new manager ends after just one year. For this reason, users need to have time to take advantage of all the functions offered to them, if the user needs it.
With the help of True Key, it is possible to identify and immediately get rid of passwords stored insecurely in the browser. The program also carries out an operation to import passwords, the number of which is not limited even in the free version.
Additional features
This modern application manages to save multiple wallet items. In total, it is possible to perform manipulations with six species. This applies to passports, pension insurance documents, driver's licenses, addresses, and more. Each specific type of object is filled with its own data. At the same time, they contain relevant fields.
The process of working with data is similar to how credit cards are processed directly when using Dashlane. During the manipulation, synchronization of all elements between wallets is carried out.
Although the password manager does not currently support auto-fill forms with personal data, it is planned to implement this option in the near future. Developers constantly monitor the appearance of shortcomings and shortcomings in their own creation. For this reason, measures are being taken to modernize and significantly improve the software.
As soon as the user completes the setup of a new account, all the most popular sites will immediately be shown where they can save credentials. As a result, authorization is carried out, and then the capture of the entered data. In the future, you do not need to re-enter personal information about yourself, since the software will do this automatically.
The password generator is activated as soon as the user creates an account or makes adjustments to the previously created one. True Key automatically generates a secret key, which consists of 16 characters. This is a unique feature as most password managers work with a maximum of 10 entries.
If you want to open a menu with available logins, then users will have to click on the LastPass button. It is located on the toolbar in the Internet browser you are using. The peculiarity of the True Key software is that it does not create special groups, folders, tags, and so on. As soon as the user clicks on the button with the name of the password manager, access to it is immediately opened.
After that, you need to choose a specific password and login, thanks to which access to the specified resource will be open. Automatic authorization is a great option for every user. Therefore, it is so important to use special auxiliary software products.
Dedicated plugin for Android devices
It is especially interesting that there are two versions for mobile devices. Both of them will be distributed with a built-in browser. So it's very easy to jump right into internet surfing. You can just as easily perform authorization without entering data in manual mode.
Also, the process of entering a password-protected site is performed using the front camera. Such elements are found in all smartphones. Thus, the program will work on face recognition. Immediately after that, the resource will be unlocked.
Manager Features
The modern program is an excellent assistant, although it is still under development. The service is constantly upgraded by the development team. The creators provided it not only with basic functions, but also with some additional features that other similar software does not have.
The unique True Key service was tested. During the checks, it was possible to reveal that the software synchronizes between the various platforms of the devices used. The utility also offers authentication using a variety of methods.
Passwords can be imported between browsers at any time. The software supports face recognition. True Key is a real competitor to other similar software products. The application is considered the most requested password manager.
Users are accustomed to the fact that small, second-rate programs come bundled with popular software installers. Among such software, True Key stands out. What kind of program is this, what is it for and how to remove it from your computer, you can read in the framework of this article.
Functions
The program is multiplatform, can provide work in one account from several devices.
Login methods (can be combined) |
|
| Face recognition | A webcam is required. The procedure scans your face, remembers its features and, based on the analysis, determines whether to grant access or not. |
| Fingerprint | You need a fingerprint scanner. |
| Multi-factor authentication | To access the application on a PC, you need to enter a verification code from another device (for example, from a phone). |
| master password | Application access password. |
| To confirm your entry, you need to follow the link. | |
| trusted device | The program remembers the device from which you work and offers to write it to the trusted ones. If you try to log in from another device, the program will notify you about it. |
Working with information |
|
| Launchpad | After logging into your account, you can conveniently organize your work with websites. |
| Password Manager | Once enter the data and the program will automatically enter them for you. |
| Storing information about cards and accounts | Allows you to store data of electronic accounts, plastic cards, passport and other personal data. |
| Password generator | Allows you to generate a complex and strong password to protect your account or other data. |
| Facial recognition when logging into Windows | A webcam is required. The program allows you not only to store personal data in a Windows profile, but also to protect the profile itself. |
| Encryption and synchronization | The information is stored on your device, and when synchronized with another device, the AES-256 encryption algorithm is used. |
The program is not bad, it has a free version that supports storing 15 passwords. To remove the restrictions, you can purchase a paid version for 999 rubles per year.
How to delete?
Advice! The utility is distributed along with McAfee antivirus. If you installed the “full set” on a “weak” PC, then it will consume large resources, which will lead to braking and lags. To eliminate unnecessary software, see the article: "How to remove McAfee antivirus".
Uninstalling the program does not take much time:

Have questions after reading the article? Share them in the comments or use
As you know, human memory is not perfect. Every day we are faced with various information, and our memory does not always provide reliable storage of the data we need. The difficulty of remembering can be especially true when remembering passwords for sites that we regularly visit and work with. This is where various auxiliary tools come to our aid, allowing you to reliably and efficiently store passwords for such resources. One of these tools is the True Key program, and in this article I will tell you what True Key is and how to remove it from your computer, describe the functionality of this application and the features of its work.
What is true key
So what is this True Key app? This program is positioned as password manager for various Internet resources and programs. True Kay allows you to easily store all your passwords to various programs and sites, supports various password entry options, including face recognition through the camera, fingerprint reader, email confirmation, master password (master password), and password using a trusted device .

This product integrates with all popular browsers, supporting cross-device synchronization and multi-factor authentication.
The main advantage of this True Key program is that it will be enough for you to log into this password manager once, and from that time it takes over all your authentication, automatically entering passwords and protecting them with encryption.
This True Key program is known to have a limited free version (maximum 15 stored passwords) and a paid full version (costs about $20 per year, unlimited passwords). The product works with Windows, Mac OS, Android and iOS operating systems.
At the same time, competing programs are also represented on the market, such as KeePass, 1U Password Manager and others.
Where does True Key come from on your computer
In considering the question "True Key what kind of program" it is important to explain where it comes from on the computer. Very often, a program appears on a PC as a result of bundling, when others are installed along with the main program, like the one described here.
An example of this is the installation of True Kay along with the installation, when the latter is downloaded from its official website. By default, along with Adobe Flash, the user receives a "makeweight" in the form and True Key, which are also installed on the user's computer and start working.

The average user rarely installs such programs (you can download True Kay from the Intel website, as well as in the corresponding stores for Android and iOS), because if this software got on your computer without your desire, then you should consider removing it from your PC .
How to work with True Key
The story that this is True Key would be incomplete without a description of how to work with this program. Download and install the application (the corresponding link to the Intel site is just above), create a master password, import passwords from your browser if necessary, and now True Kay will store and protect all your passwords.
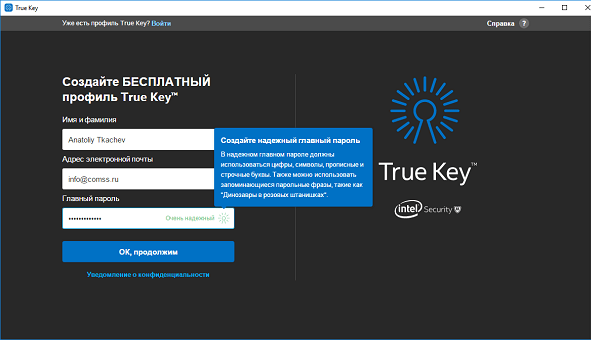
When visiting sites with already saved passwords, the manager will enter authentication data for you, and when creating new passwords, True Kay will use a special password generator that will generate a password from 16 different characters.
How to get rid of True Key
With all its advantages, the True Key program is often considered an unwanted guest on user computers. Some antiviruses define it as "unwanted software", face authentication does not always work correctly, the program constantly hangs in the background and loads the computer - in general, it has enough minuses.
Therefore, if you think about the question “how to remove True Key?”, Then the answer to it is very simple.
- Close all open browsers, go to the "Control Panel".
- Select Uninstall a program.
- Find "Intel Security True Key" in the list of installed programs and click on it to uninstall the program.

If suddenly the standard removal mechanism for this product did not help, then you should use the CCleaner program toolkit. First, stop the process itself (press Ctrl+Alt+Del, launch Task Manager, go to the Processes tab, find the Intel Security True Key process, click on it, and then click on End Process at the bottom), then launch CCleaner , go to the "Tools" tab there, select "Uninstall programs", find and remove True Key.
Also, it would not hurt to uninstall the program (in the standard way) called McAfee Aplication Installer, there is a possibility that it can reinstall True Key on your computer.
Video review
In this article, I considered the question - True Key, what kind of program and how to remove it from your PC. First of all, it may be necessary for those users who work with many sites at the corporate level, where remembering all the passwords is really quite difficult. Ordinary users who use a minimum of passwords are unlikely to need True Kay functionality, so I would advise you to remove this product using the standard method described just above.
It is already a familiar fact that along with useful software come less useful programs that are included in the overall package by developers. True Key Intel Security is also referred to this type. This utility is an Intel product and its purpose is to securely save user passwords.
The application has two kinds:
- Browser extension;
- OS applications.
It is the extension that allows you to save passwords and names for different sites and accounts in the browser and automatically fills in the authorization fields upon re-entry.
Functional
Thanks to this program, you can not write data somewhere, which greatly simplifies and speeds up the authorization process. At the same time, True Key has high security indicators and uses the AES-256 algorithm in its functionality, which securely encrypts data. 
To application features applies to:
- Ability to work in one account from different devices;
- Combined login methods: face recognition, fingerprints, multi-factor user verification with codes;
- Conveniently organized work with websites;
- Preservation of banking information;
- Password generator;
- Encryption and synchronization.
However, not everyone likes that their data saved in the system, especially if one device is used by several users at the same time.
Ways to enter the system
Since True Key Intel Security is a product of Intel and McAfee, it is naturally distributed through their software, most often antiviruses. But it can also be downloaded separately as a standalone application, which is considered by some antiviruses (most often Avast) as a virus. Also, the utility can get through:
- driver update Intel, if the PC runs on their chip and with "native" software that automatically launches update programs;
- as affiliate product in packages with other applications.
As soon as the utility is installed in the system, it automatically starts autoloading and starts every time the system is rebooted. Therefore, you will have to disable it, if necessary, every time you start the OS.
How to uninstall a program
The easiest way to uninstall the utility is the task manager and the optimal program for optimizing and cleaning CCleaner. For removing follows:

If the True Kay application is not removed in this way, you can use control panel:

These two methods most often help to permanently remove the utility from the system. It should be remembered that after this you will most likely have to enter all the data during authorization yourself.
Complete removal of a user
If the True Kay program was initially useful, but after the user decided to get rid of it, then, in addition to deleting it from the PC, he will have to delete your profile on the official site of TrueKey. You can do this by contacting the technical support of the site for help. After deleting the profile, you should clear the credential folder:
- Go to the official website of the utility;
- Open Credential management– Editing;
- Make adjustments and click " Save»;
- Remove the application from the PC using the above methods.
When uninstalling, remember that all browsers must be closed, and immediately after uninstallation - be sure restart system.
In the process of working on the network with various downloaded programs, an application such as True key. Some antiviruses point out the dubious reputation of this application and mark True Key that it is a virus, some skip it quite freely. If you accidentally discovered this True Key program on your PC, then I recommend that you study the material below, in which I will tell you in detail what True Key is, describe its main features, and also explain how to uninstall True Key from your computer .
The full name of this software product is True Key Intel Security, and the developers include such "bison" IT as Intel and McAffee. The application itself consists of two parts, the first part is installed as a regular program through the "Control Panel", and the second is an extension for your browser (Firefox, Chrome, IE, etc.). Due to the fact that the creator of this software is McAffee, and I have already met its programs, I decided to remove True Key from my laptop.
- The essence of the True Key functionality is to securely remember your passwords for various sites;
- The developers assure that you no longer have to keep all your passwords in memory, this software will do all the work for you;
- Moreover, by creating your own password storage, you can synchronize it with all your devices, and carry out identification using biometric facial features, a fingerprint or a trusted device.

By the way, this True Key program exists for all common operating systems, from Windows to iOS, and is shareware (the free version remembers only 15 login-password options). The full functionality of the program is available only through payment.
How necessary is True Key
If you are worried about the security of your passwords, do not trust your memory (and it is, alas, imperfect), and are sure that multi-step password protection and strong encryption algorithms will help your security - then perhaps this True Key program will be useful on your computer. .

If you do not need such a toolkit, and until now you have not had problems with passwords, then the presence of such a program on your computer is doubtful and you better remove True Key.
Earlier, I already raised the topic of security in a blog, then I described Windows file protection technology - a DRM license.
How True Key gets on PC
The user can easily download the True Key program on the official website of the same name. At the same time, some viruses (for example, Avast) can display a message about the suspicious nature of the application, which is due to massive user complaints about True Key that came from nowhere on their computer. 
In addition to a voluntary download, this program can get on the PC as part of other utility programs, among which the set of drivers for Intel is especially distinguished. Therefore, it is necessary to avoid automatic installation of applications and carefully review which programs are offered for installation on your computer.
How to remove True Key
Despite the flurry of criticism from users, the official application is easily removed through the "Add or Remove Programs". It is enough to go there through the control panel, find "Intel Security True Key" in the list of programs, and by clicking on it, wait until the system removes True Key from your computer. After uninstallation, you will need to reboot the system.
If suddenly, for some reason, you did not manage to remove True Key, then use other means.

Conclusion
This True Key program, no doubt, can be useful for those who are afraid of losing (forgetting) any of their passwords and are willing to pay for their security. As for the free version of True Key, its limitation of 15 passwords and the imposed nature of the application itself do not add popularity to the program, therefore I suggest deleting such software from your PC so as not to load your system with unnecessary applications that you do not need.
In contact with



